Technology
Sep 12, 2023
Fortifying the User Interface: Tackling CSRF and XSS Challenges Head-On

In today’s interconnected world, online security threats have become increasingly prevalent. Despite being aware of potential risks, even the most cautious internet users can find themselves victims of cyberattacks. One should be very vigilant of the links we click, the sites we visit, and the information we share on the forms and comment boxes. Sometimes the seemingly innocent link like a cat picture could be a devious trap.
In this article, we are going to explain the two major vulnerabilities that have affected major brands. The Cross-Site Request Forgery and the Cross-Site scripting (XSS) attack. We shall explore their execution, their repercussions, and potential measures to address them.
Cross-Site Request Forgery (CSRF)
CSRF stands for Cross-Site Request Forgery. It is a type of security vulnerability that allows an attacker to trick a victim into performing unwanted actions on a web application in which the victim is authenticated. CSRF attacks take advantage of the fact that web applications often rely solely on the authenticity of a request, assuming the request comes from the user.
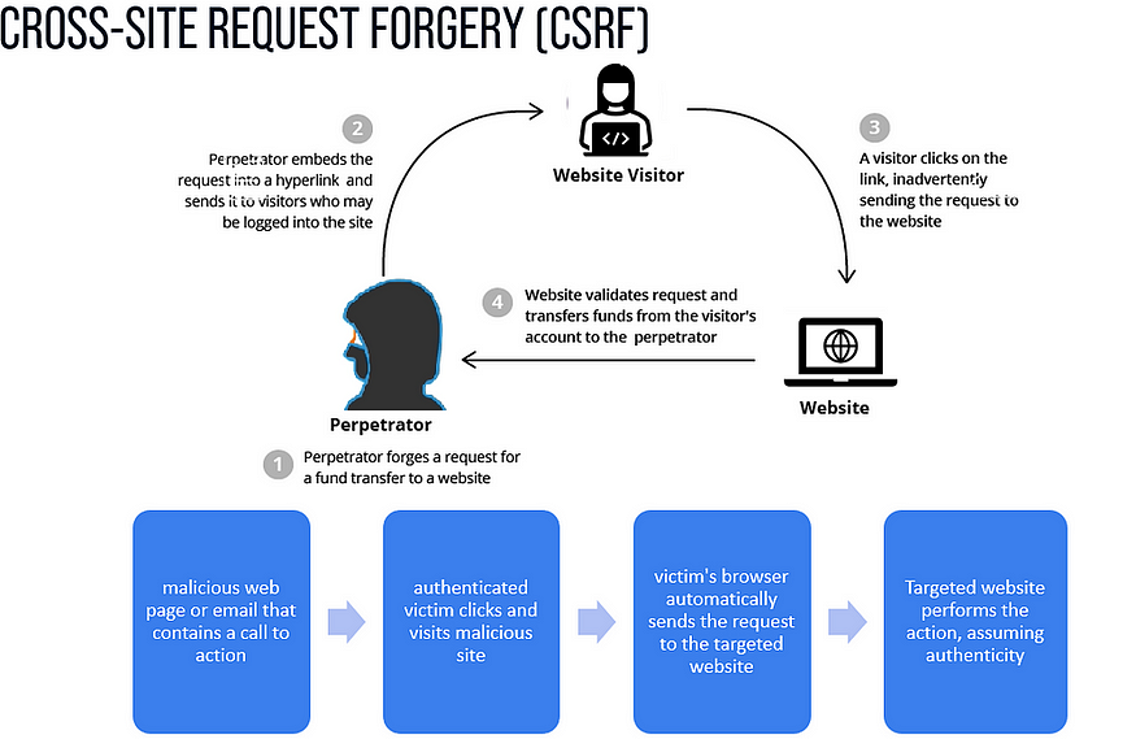
Credit: Imperva
CSRF Incidents in the Past
Apple (2015): The Page Loading functionality in WebKit in Apple Safari before 6.2.7, 7.x before 7.1.7, and 8.x before 8.0.7, as used in Apple iOS before 8.4 and other products, does not properly consider redirects during decisions about sending an Origin header, which makes it easier for remote attackers to bypass CSRF protection mechanisms via a crafted web site.
Microsoft (2015): A vulnerability in Office 365 allowed attackers to create malicious macros in documents without the user’s knowledge. It could have led to the execution of arbitrary code on the victim’s system.
Mitigating the Risks of CSRF
To mitigate CSRF attacks, the developers implement various security measures, such as:
Implementing anti-CSRF tokens: Web applications can generate and include unique tokens with each request. They are validated on the server side to ensure that the request is legitimate and not the result of a CSRF attack.
Using SameSite cookies: SameSite cookies restrict the sending of cookies in cross-site requests.
Implementing additional authentication steps: Developers can require users to re-authenticate for sensitive actions or use multi-factor authentication to add an extra layer of security.
Input validation and output encoding: Validate and sanitize all user input to prevent common attacks such as cross-site scripting (XSS) and SQL injection. Ensure that any data displayed in the UI is properly encoded to prevent script injection or content spoofing.
Cross-Site Scripting (XSS) Attack
XSS (Cross-Site Scripting) is a web security vulnerability where malicious scripts are injected into web pages viewed by other users, potentially leading to data theft, website manipulation, or other harmful actions.
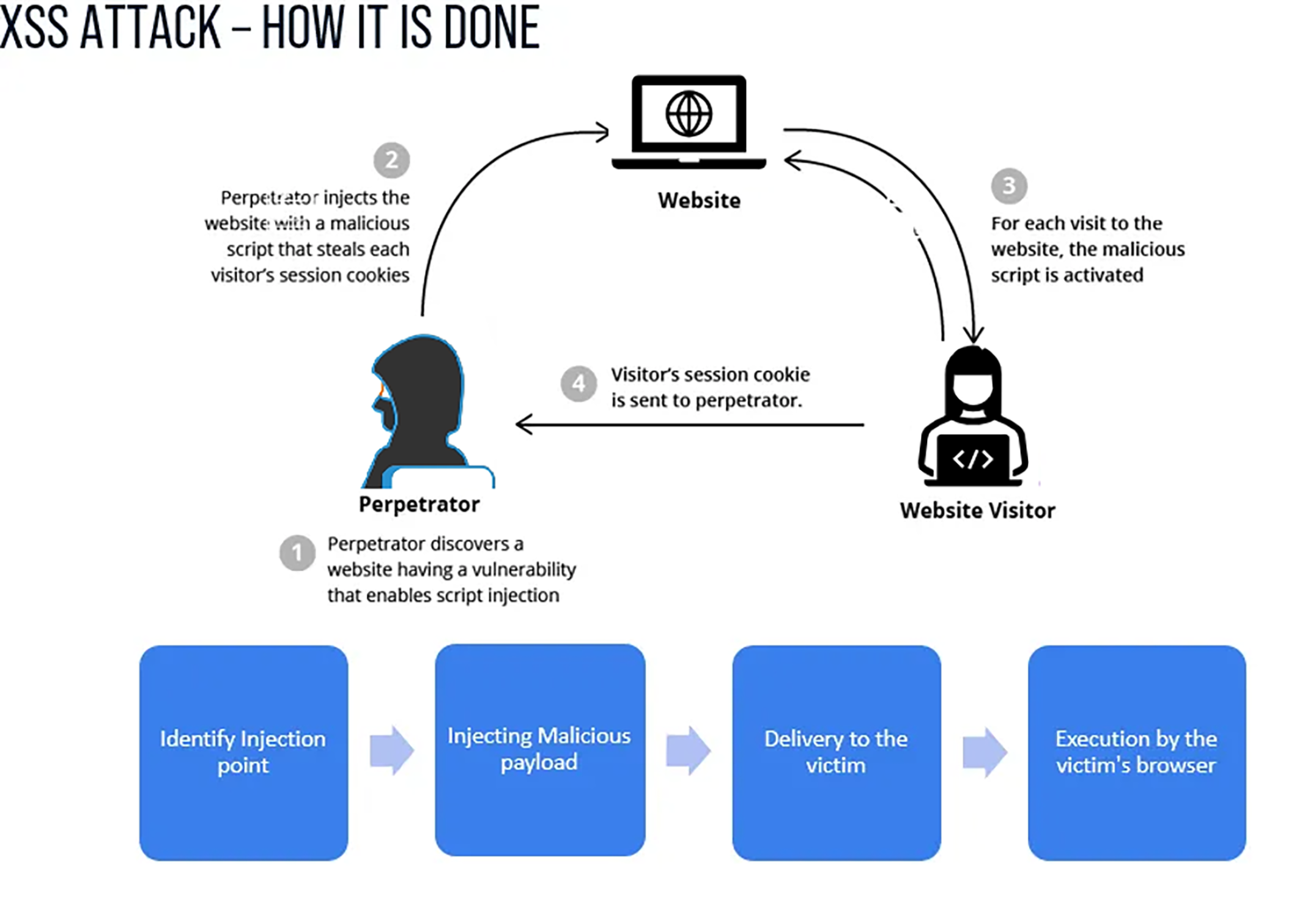
Credit: Imperva
XSS Incidents in the Past
eBay (2015-16): In late 2015 and early 2016, eBay experienced a severe XSS vulnerability due to improper validation of the “URL” parameter, which allowed attackers to inject malicious code into the platform. This vulnerability granted attackers full access to eBay seller accounts, enabling them to sell products at discounted prices and steal payment details.
The attackers exploited the vulnerability to manipulate high-value product listings, including vehicles. Although eBay eventually fixed the vulnerability, follow-on attacks persisted until 2017.
British Airways (2018): British Airways fell victim to a Magecart attack. Cybercriminals performed credit card skimming on 380,000 booking transactions. They manipulated the website’s script to send sensitive customer data to a malicious server, cleverly using a domain name that resembled British Airways.
Fortnite (2019): The popular multiplayer game Fortnight, with over 200 million users, encountered an XSS vulnerability. This security flaw enabled attackers to illicitly access the data of all Fortnite users.
How to Mitigate XSS Attacks
A successful XSS attack can lead to various negative outcomes, such as stealing user credentials, hijacking sessions, defacing websites, distributing malware, redirecting users to malicious sites, or performing actions on behalf of the user.
Considering the serious consequences, it is crucial to incorporate a layered security approach and stay vigilant to mitigate these risks effectively.
Input validation and output encoding: Implement strict validation of user input, filtering out suspicious or malicious characters. Use encoding techniques when displaying user-generated content to prevent it from being interpreted as code.
Content Security Policy (CSP): This is a security feature in web browsers that allows website owners to specify which domains are authorized to load resources on their pages. By defining these policies, CSP helps prevent malicious content injection and unauthorized script execution.
HTTP-only cookies: Mark sensitive cookies as HTTP-only. It prevents client-side scripts from accessing them. It can protect against session theft and other XSS-related attacks.
Regular security updates and patches: Keep your web application frameworks, libraries, and CMS platforms updated. Apply patches promptly to address any known XSS vulnerabilities.
Secure development practices: Follow secure coding practices suggested by OWASP. Validate and sanitize user input at every stage of your application. Avoid using functions like eval() that can execute user-supplied code.
Educate users and developers: Train your application users and developers about the risks and impacts of XSS attacks. Train the developers on secure coding practices. Caution against clicking on suspicious links or opening attachments from untrusted sources.
Security testing: Security testing is vital for maintaining robust web applications. Regularly conduct security assessments, penetration tests, and code reviews to detect and remediate vulnerabilities effectively. Incorporate automated vulnerability scanning tools to enhance the efficiency and thoroughness of the testing process.
Conclusion
Security is a collective responsibility. Close collaboration with other team members, including back-end developers, security experts, and project managers is essential to ensure comprehensive security throughout the software development process.
At Credera, we follow DevSecOps, integrating security at every stage of the software development lifecycle. This means that security considerations are not treated as an afterthought or a separate phase but are seamlessly integrated into the entire development and operational processes.
Our developers and team leaders undergo training through a secure developer training program. We utilize the Secure Code Warrior (SCW) eLearning platform, which is specifically designed to provide insights into code vulnerabilities, how to identify them, and most importantly, how to improve code hygiene to minimize their occurrence in the code base. By adopting these practices, we aim to build and maintain secure and robust software solutions for our clients.
Contact Us
Ready to achieve your vision? We're here to help.
We'd love to start a conversation. Fill out the form and we'll connect you with the right person.
Searching for a new career?
View job openings


